Data Breaches
- Overview
- Guidance, Documents & Policies
- Checklist
- Examples of Breaches
- Examples & Advice
- FAQs
- Ask a Question
Need to report a data breach? Use the Breach Log.
This best practice area pulls together all our relevant content on data breaches.
This includes:
- Data Breach Procedure
- e-learning and drip-feed posters
- FAQs
- Links to other relevant best practice
Data breaches should be kept at the forefront of your data protection planning, as they can result in the most disruption and harm.
Why?
The GDPR introduced a duty on all organisations to report certain types of a personal data breach to the relevant supervisory authority (The ICO). This must be done within 72 hours of becoming aware of the breach, where feasible:
- If the breach is likely to result in a high risk of adversely affecting individuals’ rights and freedoms, individuals must also be informed without undue delay;
- Organisations should ensure they have robust breach detection, investigation and internal reporting procedures in place. This will facilitate the decision to notify the ICO and/or the affected individuals;
- Organisations must also keep a record of any personal data breaches, regardless of whether they require notification to the ICO.
Always log your data breaches and get in touch with DPE if you require urgent assistance at dpo@dataprotection.education
Guidance and procedures
document Data Breach Procedure (5.18 MB)
Also review Information and Cyber Security Best Practice Area
Log a data breach
To report data breaches - use the Breach Log
spreadsheet
Data Breach Assessment Matrix
(5 KB)
Letter templates
document Data Breach Notification Letter to Data Subject (8 KB)
Related Best Practice Areas
Drip-feed posters
| Recognising a data breach | Responding to a data breach | |
 |
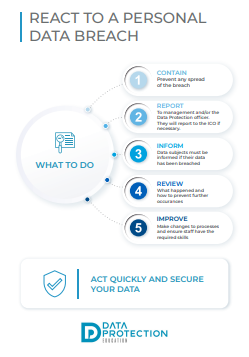 |
e-Learning
Learning nuggets:
External links
Information Commissioner's Office: Personal data breaches
Examples of breaches
- Loss or theft of paper records or loss or theft of equipment on which data is stored, e.g. a laptop, mobile phone, tablet device or memory stick;
- A letter or email containing personal and/or confidential data sent to the wrong address (including internal staff or third parties) or an email to an unauthorised group of email boxes;
- Personal data disclosed orally in error in a meeting or over the phone – including “blogging”, where information is obtained by deceiving The Organisation or where information has been disclosed without confirming the true identity of the requester;
- Unauthorised access to information classified as personal or confidential, e.g. attaching documents to an outlook diary appointment that is openly accessible;
- Posting information on the world wide web or on a computer otherwise accessible from the Internet without proper information security precautions;
- Sensitive information left on a photocopier or on a desk in County Council premises;
- Unauthorised alteration or deletion of information;
- Not storing personal and confidential information securely;
- Not ensuring the proper transfer or destruction of files after the closure of offices/buildings, e.g. not following building decommissioning procedures;
- Failure to safeguard/remove personal data on office equipment (including computers and smartphones) before disposal/sale.
Examples of Breaches caused by IT Security Incidents:
- Unauthorised access to IT systems because of misconfigured and/or inappropriate access controls;
- Hacking or phishing attacks and related suspicious activity;
- Virus or malware attacks and related suspicious activity;
- ICT infrastructure-generated suspicious activity;
- Divulging a password to another user without authority.

ICO: Learning from the mistakes of others report

Why Data Should Stay Put: Benefits of Keeping Data in Its Original System

The Perils of Paper: The Printing Vulnerability

Cyber Attack on a School

The Mother of all Breaches

ClassCharts Possible Data Breach

Where is your data stored?

If you suspect a financial scam .....

The ICO reprimands a Multi Academy Trust

Lettings Best Practice and Guidance

Where's Harry the Hacker?

The ICO Reprimands a school

How to contact us for support, subject access requests, data breaches and FOI's

Secure file transfer of files using Royal Mail

Headteacher fined for breach of data protection legislation

Cyber Security Breaches Survey 2024 (Education Institutions)

Cyber Security Breaches Survey 2024 (Businesses and Charities)

Update on Advisory for Rhysida Ransomware

The Crime in a Cyber Attack and a Data Breach

ICO Reprimand: company suffered a ransomware attack

Email and Security: ICO recent guidance

Cyber Attack: Exam Boards

VICE SOCIETY - Ransomware attacks on schools

Cyber Attack: Manchester University

Cyber Attack: Leytonstone School

Be Cyber Aware: Cyber attacks and transparency. A no blame culture

Cyber Security Breaches Survey 2023

January Cyber update - How Can Schools Help Prevent Cyber Attacks?

Emails – good practice and minimising the risk of a data breach
Have a question about data breaches? Ask it here.
Please use this for generic questions about breaches and breach procedures.
To report a data breach - use the Breach Log
To contact use about an urgent or specific query contact us using: dpo@dataprotection.education
